Top 10 Things to Do After Installing Kali Linux
Kali Linux, by default, probably doesn't have everything you need to get you through day-to-day penetration testing with ease. With a few tips, tricks, and applications, we can quickly get started using Kali like a professional white hat.
Most Linux distributions are highly customizable. This makes personalizing your penetration testing distribution a bit daunting. With just a few commands, we can automate tasks, install our favorite software, create additional user accounts, properly configure anonymity software, and optimize our interactions with terminals. There are just a few things we can do to improve our interactions with the operating system.
2Configure Bash Aliases
Bash aliases are fantastic for creating customized command line shortcuts. For example, we can reassign the ls command to automatically use our favorite arguments. Below is an example of a normal ls output.
Here it is again after creating an ls alias.
We're getting a much more verbose output. The ls command is now using the -l, -a, -t, -h, and -r arguments automatically. All of these arguments will instruct ls to use the listing (-l) format, list all (-a) files — including hidden files — and print the file sizes in human-readable (-h) formats (e.g., 1K, 234M, 5G).
My alias will also sort the output by modification time (-t), and reverse (-r) the order of the list so recently modified files appear at the bottom of the terminal. This collection of arguments is my personal ls preference, but yours may be different.
To create aliases, open the /root/.bash_aliases using nano or your favorite text editor. Add the following line to create an alias.
We can also go a bit further and add more complex functions to the .bash_aliases file. Below is a simple example of a function designed to keep Kali fully up to date.
After saving changes made to the .bash_aliases file, open a new terminal for the changes to take effect. Running the newly created apt-updater function will invoke a series of apt-get commands that will automatically update and maintain your system. The ampersands (&&) ensure that the function doesn't continue to the following command if a prior command fails.
For more on Bash aliases, check out Kody's "Set Up a MacOS System for Wi-Fi Packet Capturing" article.
3Create a New Low Privileged User
Many applications like the Chromium Browser and the Tor Browser should never be opened or used as a root user. Such applications rely heavily on low-level permissions to deliver some degree of security. It might be beneficial to some users to create a low privileged user account for such activities.
This concept is covered in greater detail in Takhion's "Lock Down Kali Linux for Safe Desktop Use" article, so make sure to check that out for help.
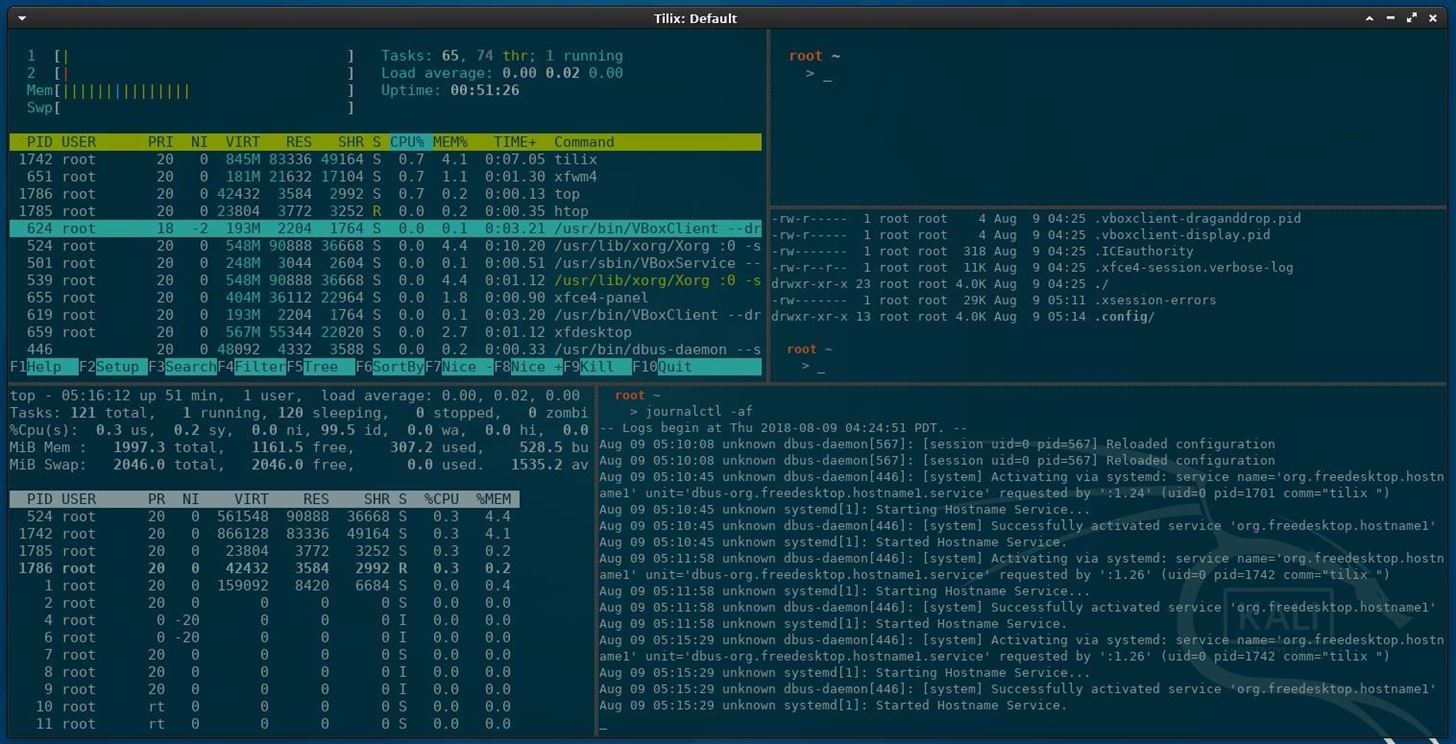
4Install a Terminal Multiplexer
A multiplexer is a tiling terminal emulator that allows us to open several terminal sessions inside one single window. The major benefit to this is being able to see all of our open terminal sessions at once and not layer the windows on top of each other. Below is a multiplexer example.
There are many noteworthy multiplexers. Tilix, as seen in the above screenshot, is an open-source and reliable option. Alternatives include tmux and screen.
Tilix is available in Kali's APT repositories and can be installed using the below command.
5Install Your Favorite Hacking Tools
Some versions of Kali are geared toward minimalist pentester's who prefer not to have hundreds of hacking tools preinstalled. This means we'll have to install our favorite tools manually. The types of tools we use vary based on our skill set and areas of expertise, but below are some popular hackings tools.
- Aircrack-ng: Wireless WEP/WPA cracking utilities.
- BeEF: Browser exploitation framework via web applications.
- Burp Suite: Graphical application designed for web application security.
- Hydra: Login password brute-forcing utility.
- Nikto: Web server security scanner.
- Maltego: Open-source forensics and intelligence gathering.
- Nmap: Port scanner and network mapper.
- Wireshark: Graphical application for network traffic analysis.
These tools can be installed using the below command.
6Install the Latest Version of Tor
Tor is available in Kali's repositories, but anonymity software should be acquired directly from the source (torproject.org). Furthermore, Kali's version of Tor is not reliably maintained or updated. This means we could be missing critical stability and security updates.
Add the Tor Project repositories to your APT repository list.
Then, download the Tor Project package signing key and import it into your APT keyring.
You'll see the "OK" output when the signing key has been added to your keyring. Next, update APT using the below apt-get command.
Install Tor using the below command, and you're done.
7Configure File Sharing with Syncthing
Syncthing, created by Jakob Borg, is a cross-platform, private, lightweight file-syncing (Dropbox) alternative. As a penetration tester, transferring keystroke logs, screenshots, webcam recordings, and sensitive loot files between virtual private servers and local Kali machines can be a frustrating task. Syncthing makes secure file-sharing totally painless.
I've covered the Syncthing installation and configuration in a previous article. Readers should reference that for a detailed step-by-step guide.
8Install a Code Editor
Atom is a free, open-source, feature-rich, and highly customizable text editor. Its features include the ability to collaboratively share code in real time, intuitive coding autocompletion, and the ability to install packages which further enhance Atom's versatility. Other noteworthy text editors include Geany and Gedit.
To install Atom, head over to their website and download the latest Debian installer. Next, open a terminal and install the required dependencies using the below apt-get command.
Finally, use dpkg, a command line package manager, with the install (-i) argument.
When that's done, Atom will be available in your Applications menu.
9Clone Rubber Ducky Encoder
The USB Rubber Ducky is the notorious keystroke injection tool. Creating ducky payloads is easy using the DuckToolKit website, but as a penetration tester, it's unsafe to share client information with random websites. Uploading payload contents to a third-party website can be dangerous.
Instead, we can use Git to clone the USB Rubber Ducky repository and encode payloads locally.
Then, change (cd) into the USB-Rubber-Ducky/Encoder/ directory and use the following java command to start encoding ducky payloads without third-party websites.
10Change SSH Keys & Default Password
The default password for every Kali Linux installation is the same (toor) which makes it very easy to automate attacks. Also, the default SSH keys can allow an attacker to intercept your communications when you're controlling something like a Raspberry Pi via SSH.
To change the SSH keys, first, change into the directory. Doing the below two commands will reset the SSH keys from the default ones.
Now, for your Kali system's password, enter password root, then enter in your new password. Afterward, retype it to confirm. If you're not logged in as root, you may be asked for your current password before doing this.
What's the First Thing You Do After Installing Kali?
We all have varying degrees of interests, skill sets, and levels of experience. Which makes compiling a well-rounded list of post-installation steps tricky. Did I miss any critical steps? How do you personalize and customize new Kali installations? Be sure to leave a comment below.
Comments
Post a Comment